Database Encryption
Database Encrypting
Data security is one of the typically most important requirements as data are fast moving into cloud environments – Ransomware are becomming more and more a big issue for companies – almost all the major companies likle Adobe, Facebook and similar have been attached and their data have been taken.
Hackers will normally ask for large sums to give the companies access to own systems as well as not to be sharing their data on the internet.
To test own email address and be validating it it have been shared with associated data like example password and similar go to https://haveibeenpwned.com/ Enter email address and see if own email is in one of the major hacks where the hackers have shared the customers data.
Encrypting the data in the associated systems prevent the hackers from gaining direct access to the data inside the database as well as when being send between nodes.
We are experts in handling database encryption IN-REST as well as IN-TRANSIT – basically delivering an extremly strong data protection that prevent enternal sources to be getting direct access to the companies key data.
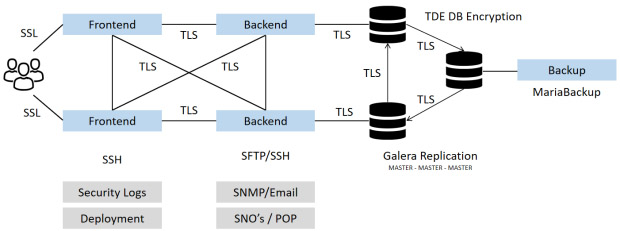
This extra security level do we now offer companies to deliver enhanced database security using In-Transit protection as well as In-Rest protection, meaning communication between the database and back end will be using TLS tunneling with a certificate added and the actual database and important files being on the fly encrypted.
Ransomware Protected
The new trend in providing remote worker access and having IT moving into the cloud environments do mean that a higher degree of security is needed for companies – protecting the companies key data is essential and do demand database encryption like described to protect.
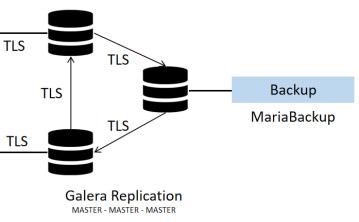
Backup with Encryption
Performing backup of a databse environment that is encrypted demand special requirements – we will be able to be guiding the customer.
Database backup is managed using two in dependant backup solutions, first is complete database backup performed using a server image snap shoot taken every xx hours – this type of server backup is fast and allow extremely fast recovery in case their is an issue taking place.
IN-REST Security (TDE)
At-rest encryption means the data-at-rest like data files and logs are encrypted on the disk, makes it almost impossible for someone to access or steal a hard disk and get access to the original data (provided that the key is secured and not stored locally).
Data-at-Rest Encryption, also known as Transparent Data Encryption (TDE), is supported in example MariaDB 10.1 and later – we will typically perform upgrade from 10.1 to version 10.3 to get all the latest security patches added at the same time when applying encryption. Note that using encryption has an overhead of roughly 5-10%, depending on the workload and cluster type installed.
For MariaDB as an example, the following MariaDB components can be encrypted at-rest:
- InnoDB data (shared tablespace or individual, e.g, *.ibd-ibdata1)
- Aria data and index files.
- Undo/redo logs (InnoDB log files, e.g, ib_logfile0 and ib_logfile1).
- Binary/relay logs.
- Temporary files and tables.
The following files can not be encrypted at the moment:
- Metadata file (for example .frm files).
- File-based general log/slow query log.
- Error log.
Data at rest encryption requires the use of a key management and encryption plugin, we will be generating the needed key file to be used with openssl and then configure At-Rest Encryption.
IN-TRANSIT Security
Communication between backend and database environment will not be encrypted if or when the database in installed on the same environment as the backend nodes as all connectivity are taking place inside the node. Where having database servers installed in a seperate setup like with our Galera replicated database model will database nodes typically be on seperate server – here can TLS be added to the server to server connectivity – also called In-Transit encryption.
Used tunnel setup isn’t standard SSL but TLS that provide a higher degree of security – we are typically using TLS version 1.2 eventhen the upgraded database version will support version 1.3.
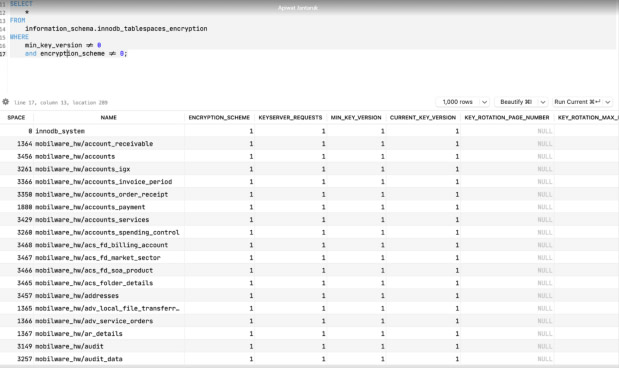
Below indicate with “1” that database is encrypted: