Secure Forms
Web Service Protection
Online security is a bit of a hot topic these days. Not a day goes by where some poor business has their website hacked and their users’ data stolen. This can spell disaster for even the strongest of businesses out there.
While you might not think anything like that could happen to you, every other victim of hacking thought exactly the same. Online attacks can affect any business, big or small.
Therefore, website security measures are or at least should become a priority for you. If you deal with customer data, or even payment details, this makes it all the more important that you do something about your security. When you’ve got data like this, you inevitably become more of a target.
If you have a self-hosted web server that offer web pages as well as forms, then is your website’s and form interfaces security your responsibility. If you can’t protect your users’ data, you could run into more than just security issues.
One area of concern you should be having is with your online forms as it is a very difficult task to provide the needed form protection.
Web based forms are such an important part of any business website now, that they can’t afford to be overlooked. If not properly maintained they can become the weak link in your otherwise smooth business operation. We mainly deliver our expertise for Drupal and WordPress – the two most used Open Source web sites.
Protect your forms
Spam Protection
there are 2 types of spam. First one is spambot which is programmed to abuse all web forms it can reach, leave comments about some product and spread the links. The second type of spam is organizing manually by people who were hired to spam targeted sites. It is more difficult to divine their actions because they can get around the defense systems. So, first of all, you need to get a get a good contact form which will provide all necessary means to protect your site form the spam. Now, let’s get back to it and consider the ways that will enhance the spam protection:
Install CAPTCHA plugin
CAPTCHA is one of the most prevalent and popular ways of spam blocking. This script is designed to generate randomly selectable texts or more complicated expressions which are displayed in such way that makes it hard to decipher it for spambots (in some cases even for the humans as well). If the user enters the data correctly he will be able to fill in the form and you won’t be overwhelmed with tons of spam, but do not overdo with CAPTCHA. Set it on the most significant forms, otherwise, your visitors might be scared away by constant verifications.
Do not use auto-responders
When a user fills in the form he can get an automatically sending
Email with words of gratitude for registration or something like that
and this is a powerful weapon for spammers. Instead of this you should
better reply to everyone personally and disable auto-responders to
prevent “over spam”.
“Honey Pot” – a trap for spambot
This method is based on the statement that bots cannot recognize CSS
or JavaScript, so it is possible to create the forms that will be
invisible for the customers but “available” for the spambots which can
read only the HTML. The robots will be attacking the HTML with a couple
of prepared Emails while the real forms remain intact. But be careful,
spambots are getting more complicated, so there is no 100% guarantee
that they won’t circumvent such defense.
Limit the login attempts
You can reduce the spam number by installing Limit Attempts plugin which will allow you to set the number of failed login attempts and block user’s IP, so you can stop automated scripts and protect your
website.
Use test questions
The idea consists in putting a simple question which would be easy to
answer for a human, but which will cause the problems for the bot. It
is usually a simple math problem or a well-known question like “What is
the color of the tomato?”. If you get an incorrect answer, you’re
probably dealing with a spambot (or a guy, who doesn’t know how tomato looks like, which is very unlikely), so block the access and stay calm.
Try to embed session tokens
Considering that bots don’t set cookies, you can prevent spam attacks
by setting the session tokens. If the session cookie wasn’t set on the
form, so only the people will be able to fill it out because the most of
spambots attack the forms directly and this measure will help to get
rid of them.
Use special tools like Akismet
Akismet is an efficient tool that will help you to block spam on your forms. Generally, it is very popular among the bloggers because the tool is doing its job great when you’re
dealing with comment spam, but the other forms can be protected too. The most distinguishing feature about Akismet is an ease of use, so you can set it on and relax while it will defense your forms automatically.
Check your IP filter
When you receive a spam you can get the IP addresses from which it
was sent. A list of these addresses will help you to monitor and filter
the incoming requests so the next time you could deny it and protect
your forms from spam attacks.
Authentication
Authentication and authoritisation is an important part of most form interfaces security. Authentication will validate the users credentials and figure ourt what functionality and what interfaces a given user is authorized to access but after authentication is it as well highly important to perform form protection to prvent authenticated users from performing unwanted data injections.Protecting forms after authentication is often one of the forgotten security elements as the owner think that authenticated users don’t inject any malformated data into their forms.
Form Interfaces
In the Digital Transformation process will a lot of form interfaces be applied to web interfaces – protecting form interfaces can be very difficult when at the same time trying to allow users to add data, add documents and similar – the list of potential threats in this area is very large.
An example of threats is cross scripting – or data injection that turn out to be understud as code or SQL commands when hitting the backend environment.
Performing a Basic interface test can be done using example https://observatory.mozilla.org/ That will give an indication of the level of protection applied in the interface.
Below is the first sample from a setup we have done for KDDI in Japan showing that interface have all required security in place:
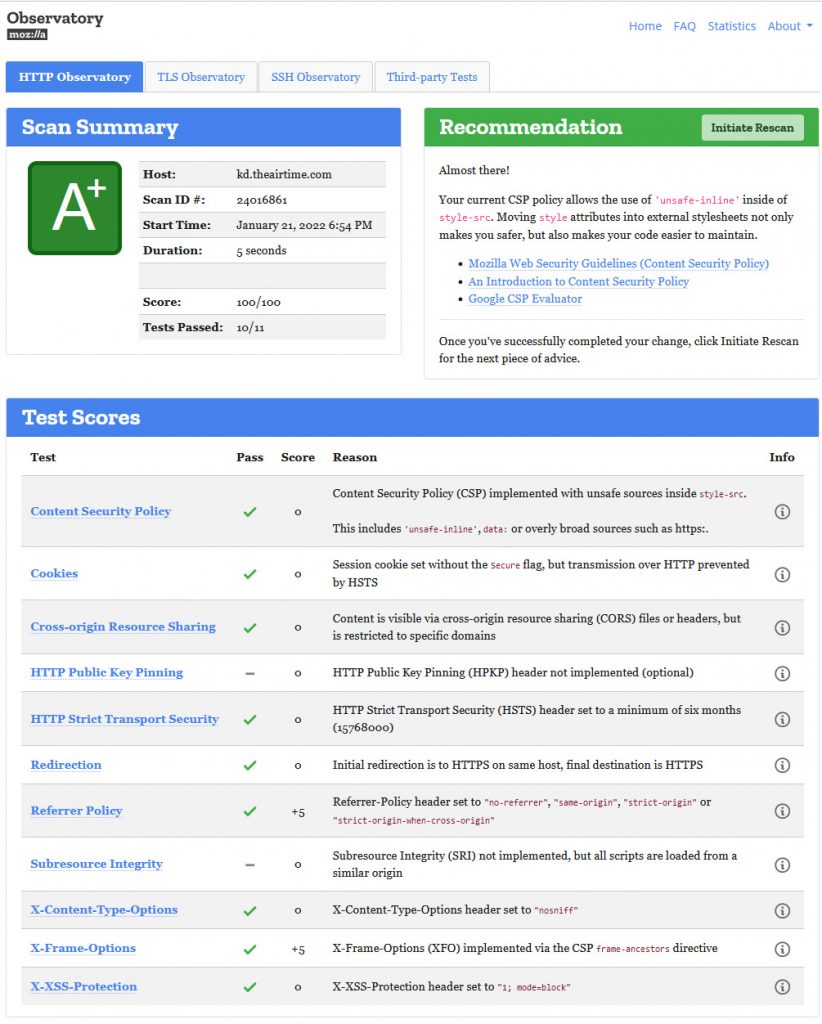
The next is illustrating another form interface handling online Thai Travel Pass requests, illustrating that these tools can be helping the user in adding the needed protection before the unwanted intruders access the system and the associated stored data:
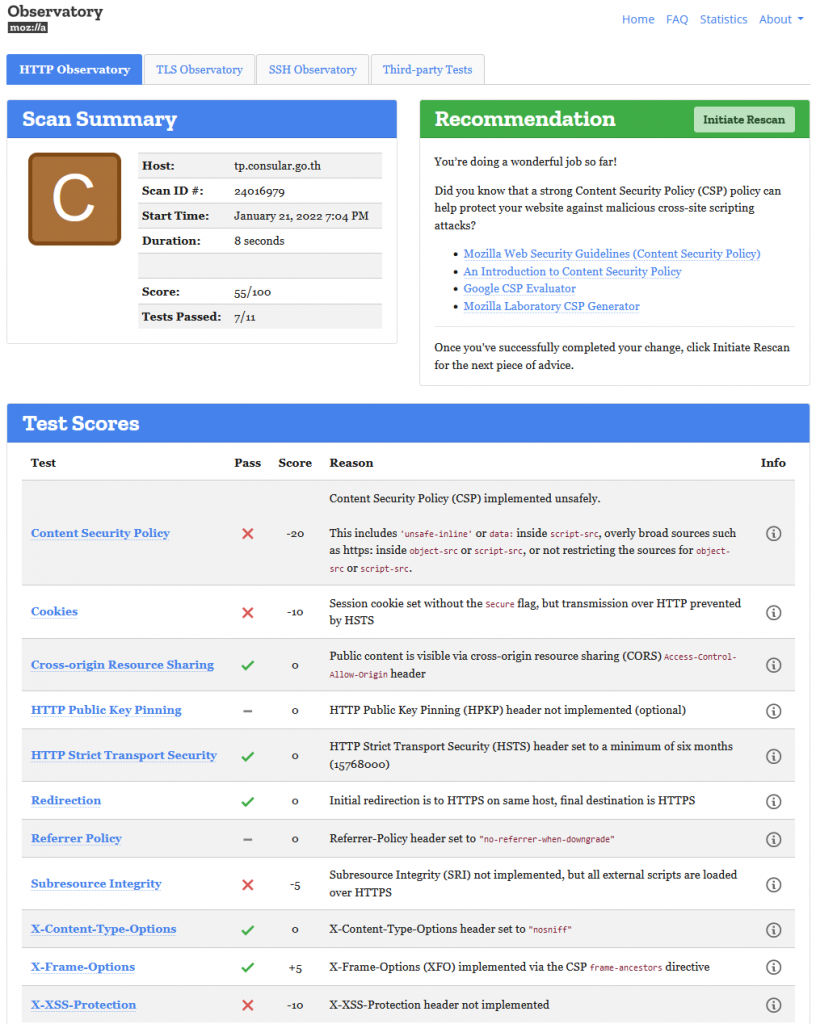
Form Data Validation
Validate data entered into form interfaces using validation rule, also perform periodiv penetration testing of the added form interface, apply authentication or even two factor authentication. We are using several scanning toold to validate the level of security implemented and example can be OWASP where we have our own server installed with OWASP software to allow scannings to take place before installing service in the open.
Input validation is performed to ensure only properly formed data is entering the workflow in an information system, preventing malformed data from persisting in the database and triggering malfunction of various downstream components. Input validation should happen as early as possible in the data flow, preferably as soon as the data is received from the external party.
Data from all potentially untrusted sources should be subject to input validation, including not only Internet-facing web clients but also backend feeds over extranets, from suppliers, partners, vendors or regulators, each of which may be compromised on their own and start sending malformed data.
Input Validation should not be used as the primary method of preventing XSS, SQL Injection and other attacks which are covered in respective cheat sheets but can significantly contribute to reducing their impact if implemented properly.
We perform both client side validation in line as well as server side validation and most important validation of any data transfered across API interfaces.
Web Server configuration
Add SSL to the connection between browser and web server – free SSL on example https://letsencrypt.com or simply by using CDN solutions like Cloudflare that offer SSL connectivity.
Implement DNSSEC on your DNS server environment, add secure header protection in your web server anensure that webserver as well as operating system have the latest software versions installed.
Apply firewall on basically all servers – software based like Juniper VSRX or simply IP tables – limit access to all not used ports and special access like SSH – make sure to be using a nonstandard port configuration.
Add autobanning software that constantly monitor your log files and automatically perform banning of unwanted access that try to authenticate or similar. Limit traffic to contries where the server have to deliver services to prevent direct unwanted remote access attempts.
