Security
With the fast ongoing digital transformation, data security is more important than ever. General and targeted attacks against organisations and individuals are prevalent and securing critical assets has become a mission critical task in the always online, completely connected ecosystem fast evolving.
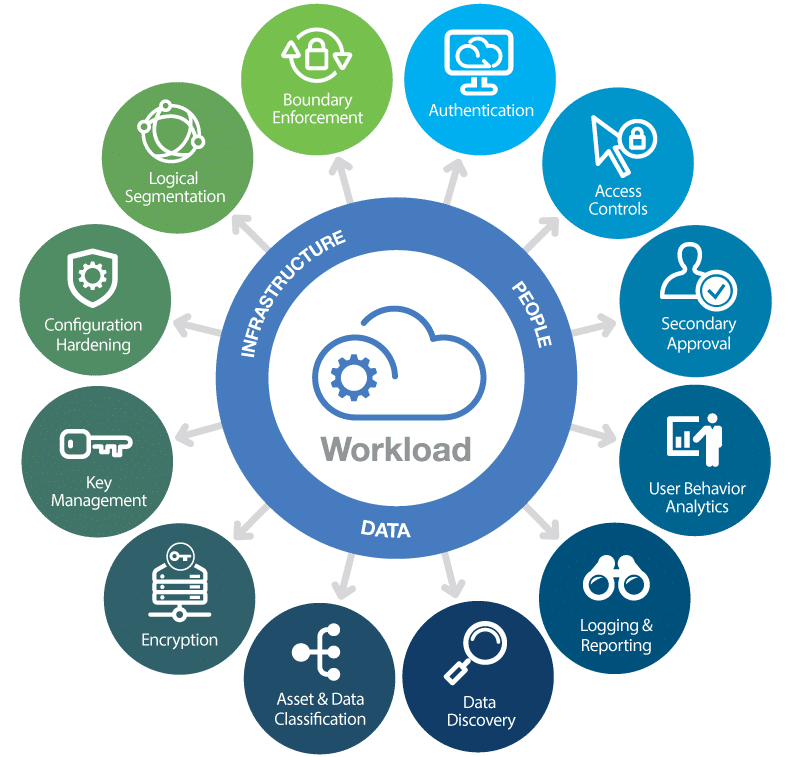
Cloud Security
The ongoing Digital Transformation are fast moving corperate IT into the Cloud or into Hybrid cloud archetecture. The old Firewall setup are not really working on a cloud implementation – where each single installed virtual server, or container /kubernetes need to be protected.
We are masters in high cloud security – read more:


Database Encryption
The number of ransomware attach are fast growing – hackers gaining access to the company data – making it public available.
We offer to encrypt databases – stand alone or clusters – like MariaDB Galera – we offer IN-REST encryption and IN-TRANSIT encryption as well as upgrade the involved backup services so they support encrypted database handling.
Secure Remote Working
As more and more employees have transitioned to be working remotely have the cybersecurity threats been increasing dramatically. Remote working offer a lot of benefits and high degree of flexibility but it present completly new security issues tothe companys IT department.


Secure Forms
Capture of data and documents through web services having self care in place are allover the world fast getting implemented – removing the need for manual processing, costly staff – but this also introduce a completly new level of security threats. Now can hackers from the complete world access the new business environment.
Secure forms demand implementation of a lot of security models – an easy way to initially perform this threat testing is to use one of the many available tools.
ISO27001 - SOC I+II
We offer our cloud environments throughout the worlkd from the 16 Biggest Internet Exchange points – all hosting are provided in military grade facilities like Equinix that provide ISO 27001 certified facilities as well as SOC I + II certified security levels.
We provide the best in class cloud and hosting facilities.

Why be using us for your security in the cloud as well as in the company?
Proven Record
We deliver military grade secure solutions to Airbus Defense, Boeing, Thales, Honeywell, L3Harris, Singtel, KDDI, NATO, IDRS for Spy satellites..
Certified Staff
Every second year will our staff undergo Comptia Security certification and Juniper Firewall certification..
Secure End to End
We cover basically all area of a companies Digital Environment, Internal, Cloud, Database, Forms, CMS, Remote working…
Your Security Partner
Cyber Secure
We ensure your digital services are implemented in a secure and safe architecture.
Threat assessment
Discover the threat level of your digital services - and get input to possible needed protection. We analyse your needs and offer physical Juniper firewalls as well as a range of software based firewalls like Juniper VSRX. We analyse the current situation as well as what threats their are to the business. Our threat assesment cover end to end IT infrastructure not including remote staff access that is covered in a dedicated service. Threat analysis across web services, forms, databases, installed software as well as network infrastructure and cloud solutions.
Secure Development
Improve your development security end to end to ensure that their is no weak points.
We are experts in building secure software with industry leading secure software development processes and practices.
Train your internal dev teams
to evaluate current development practices, improve git model and deployment model.
We will based on Ajile security processes be guiding to to a highly secure setup, whether you are developing in-house or offering services externally.
Penetration testing
Vulnerabilities exist in almost all solutions, and it is far better to find them before someone external start accessing your services.
Our penetration testing service:
- Find and report vulnerabilities
- Access to Interfaces, web, api, network..
-Access to code, config and details
Our penetration testing does not just find the vulnerabilities, but provides clear, actionable recommendations for fixing the issues, included suggested code modification.
Security assessments
It is often necessary to have external expertise for evaluating the status of your services or software, either through a straightforward code review or an in-depth assessment of the security and practices of a service.
- Validating code and workflow practices
- Benchmarking to industry standards
- Get Security recommendations
We offer a range of security validations and direct assessment of interfaces & services that will give you actionable recommendations for improvement.
Cloud security
Digital Transformation typically involve cloud solutions - private, public or hybrid.
Protection in the cloud demand typically dedicated firewalls per service, per virtual node, per container - as well as a new type of smart detection of intruders.
Most cloud providers deliver some degree of security linked to connectivity and similar but in the cloud is it highly important to understand how to protect authentication, maintain secure software versions and similar.
- Review cloud security practices
- Train operative teams
Google Cloud Security
Google cloud platform GCP have a range of security features that allow protection as well as secure authentication with a rich set of permission features. Shared security responsability, long list of security features like VCP, Data encryption, secure log access, Binary authentication, integrated IDS system, data loss prevention, Anti-DDoS, WAF, anto-bot as well as API protection.
Let our Google Cloud Experts guide you through the many possibilities and help out finding a solution that is matching your requirements – Google Secure Authentication will also support SSO.

Cloudflare Security
Cloudflare is one of the biggest CDN providers world wide – they offer advanced CDN functionality where content is hosted on own environment but distributed by Cloudflare across the world – Cloudflare will distribute content – acting as a proxy provider. They offer an advanced management interface to handle firewall settings, DDoS attack, as well as allow the user to overcome advanced attach on their interfaces. We have deep knowledge in how to be utilizing Cloudflare security.
Digital Ocean Security
Digital Ocean have local breakout in 16 of the biggest Internet exchange points – hosted at providers like Equinix having full ISO 27001 military grade security level as well as SOC I + II.
Digital ocean offer a very comprehensive security management setup across basically any of their cloud services and offer all for very agressive pricing compared top the larger players like GCP, AWS..


CMS Security
Securing the companies content management system so that it can deliver a trustred company web site demand security across many area’s.
Platform security, web server security, Script security, plugin security, framework security, page building security across crossscripting and similar. We mainly work with Drupal and WordPress that both are open source platforms and our Bootstrap based environment used for forms.
Secure Authentication
Authentication is a process of validating the identity of a user. It merely has two return values, i.e., true or false. Most authentications will be placed at the start of the system because validation is most important for any system. The system lets you enter if you’re authenticated. Authentication may vary from system to system, but everybody needs some tangible steps to make it most secure. We have delivered authentication for the biggest companies like Airbus Defense, Boeing, Honeywell, Thales, Telespazio, L3Harris all military suppliers.